| | |
| Selection Controls |
 |
|
|
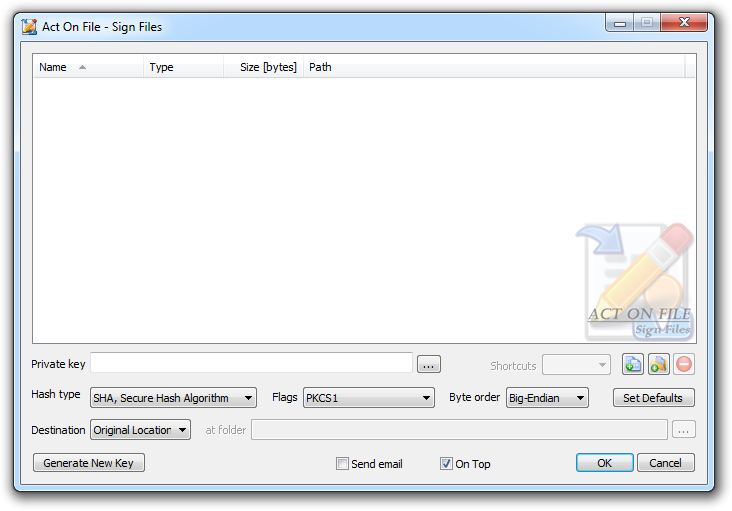
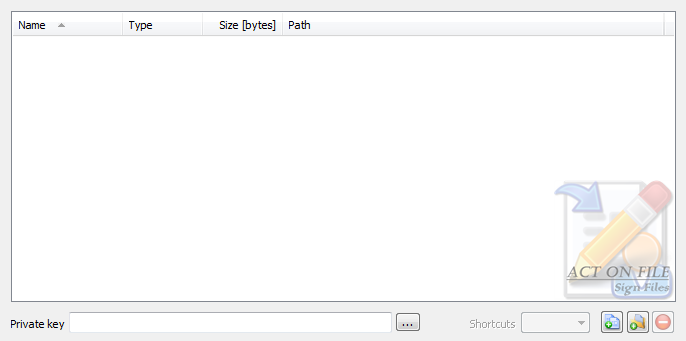
These controls are used to select and display the files and folders for the operation, and the signing (private authentication) key. In addition to the Add Files, Add Folders and Remove buttons, you can use the standard clipboard, drag and drop, and keyboard operations.
|
| Shortcuts | Select the behavior of the functionality in respect to any shortcuts that might be present in the selected folders. |
| Target | Any shortcut located in selected folder will be dereferenced and its target file or folder will be treated as if it were selected. |
| Ignore | Any shortcut located in selected folder will be ignored. |
| Private Key | Select or enter the path to the Private Key that is to be used for creating the digital signatures of the selected files. Remember to keep Private Keys safe and secret until such a time as they are to be destroyed using True Delete. |
| Operation Controls |
 |
|
|
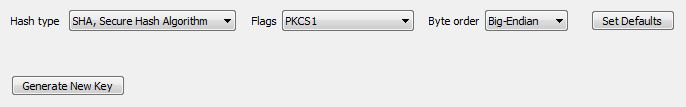
These controls are used to control the operation of the module and thus directly affect results.
|
| Hash type | Select the hashing algorithm to be used to hash the data. In order to minimize and unify their size, digital signatures are produced on a hash of the raw data and not on the raw data itself. |
| SHA, U.S. DSA Secure Hash Algorithm | This algorithm generates a 160-bit hash value. |
| MD2, Message Digest | This algorithm generates a 128-bit hash value. |
| MD4, Message Digest | This algorithm generates a 128-bit hash value. |
| MD5, Message Digest | This algorithm generates a 128-bit hash value. |
| Flags | The signing function requires that the signed data has a size multiple of a particular number. To adjust its size, the system will add padding when necessary. |
| PKCS#1 | Use PKCS#1 padding. |
| X.931 + PKCS#7 | Use X.931 + PKCS#7 padding. |
| Byte Order | The signature can be produced and exported in Big-Endian or Little-Endian byte order. The Byte Order is important when verifying signatures. Note that different platforms may have different byte orders which can cause verification failures. |
| Big-Endian | Produce signatures in Big-Endian byte order. |
| Little-Endian | Produce signatures in Little-Endian byte order. |
| Set Defaults | The Set Defaults is a user friendly button to set the Operation Controls to a default selection of properties in order help users who might find the settings confusing. |
| Generate New Key | Select this button to invoke the dialog used to generate a new Public-Private Key pair for authentication, or the Public Key of an already existing Private Key for authentication.
| Generate New Key For Authentication Dialog |
 |
|
|
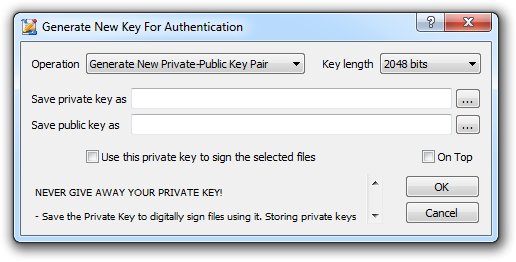
Use this dialog to generate a new Public-Private Key pair for authentication, or the Public Key of an already existing Private Key for authentication.
|
| Operation | Select whether to generate a new Public-Private Keys pair, or only the Public Key of an already existing Private Key. |
| Generate New Private-Public Key Pair | Choose this option to make the functionality generate a new set of keys with the selected key length. |
| Length | Select the length of the key that will be generated. Smaller keys are easier to break than larger ones. However, the time it takes to generate and import larger keys also increases. It also takes more time to sign files using longer keys. At present, a key length of 2048 bits is considered strong. This option is only meaningful when generating a new Private-Public Key Pair. |
| Save private key as | Choose path and filename for the newly generated Private Key. Remember that Private Keys must be kept safe and secret until such a time as they are to be destroyed using True Delete. |
| Save public key as | Choose path and filename for the newly generated Public Key. Give the Public Key to any other party, so that they can authenticate information signed and sent by the owner of the Private Key. Public Keys must be supplied in a way that guarantees that the key belongs to its owner. We publish our Public Key on our website. |
| Produce Public Key From Private Key | Select this option when a Private Key already exists, and only its Public counterpart is required. Private Keys must always be kept safe and secret, while public keys are intended to be made public. The owner of the Private Key need not always keep a copy of the Public Key, instead they could keep only the Private Key and produce the Public Key at any time and supply it to other parties as needed. |
| Source private key | Select the Private Key for authentication whose Public counterpart will be produced. Remember that Private Keys must be kept safe and secret until such a time as they are to be destroyed using True Delete. |
| Produce public key | Choose path and filename for the generated Public Key for authentication. Give the Public Key to any other party, so that they can authenticate information signed and sent by the owner of the Private Key. Public Keys must be supplied in a way that guarantees that the key belongs to its owner. We publish our Public Key on our website. |
| Use this private key to sign the selected files | Set this checkbox to copy the path of the selected Private Key into the Private Key selection control of the Sign Files functionality to be used to sign the selected files and folders content. |
| On Top | Sets and clears the Always On Top flag on the owner Sign Files window. This checkbox adds or removes the window from the group of Top-most windows. |
| OK | Commits to work. |
| Cancel | Closes the dialog without doing any work and returns the control to its owner Sign Files dialog. |
|
| Destination Controls |
 |
|
|
These controls are used to direct the output location to where the module will place the signatures.
|
| Destination | Select the output type and location. |
| Append to File | Each signature will be appended at the end of the signed file. The ".signed" extension will be added to the filename and will be the new filename extension. |
| Common Place | All produced signatures are stored in the target folder and are named "[signed filename].[signed extension].signature". Caution is required as signatures with matching names may overwrite each other. |
| Original Location | The signatures are deposited in the same folder where the signed file resides and are named "[signed filename].[signed extension].signature" |
| Reflecting Tree | The directory structure of the selected files and folders will be replicated under the selected target destination folder. Each file signature is named "[signed filename].[signed extension].signature" and is deposited in the newly created folder respective to the folder containing the signed file. |
| at folder | Select folder to be used for the "Common Place" and "Reflecting Tree" options. |
| Send email | Set this checkbox to request the module to start the default e-mail software installed on the machine and attach the signed files, or the source files and their signatures to a new e-mail message. |
| Window Controls |
 |
|
|
These controls have generic meanings.
|
| On Top | Sets and clears the Always On Top flag on the window. This checkbox adds or removes the window from the group of Top-most windows. |
| OK | Commits to work and creates the required signatures. Before work begins, an Import or Generate Signature Key(s) message will be displayed. |
| Cancel | Closes the window without doing any work. The last selected properties are stored. |