| | |
| Selection Controls |
 |
|
|
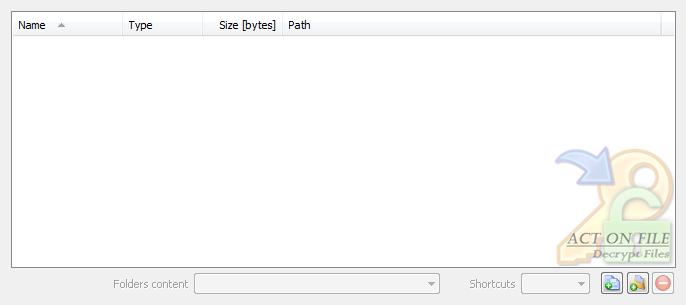
These controls are used to select and display the files and folders for the operation. In addition to the Add Files, Add Folders and Remove buttons, you can use the standard clipboard, drag and drop, and keyboard operations.
|
| Shortcuts | Select the behavior of the functionality in respect to any shortcuts that might be present in the selected folders. |
| Target | Any shortcut located in selected folder will be dereferenced and its target file or folder will be treated as if it were selected. |
| Ignore | Any shortcut located in selected folder will be ignored. |
| Folders content | Select the behavior of the functionality in respect to the files located in the selected folders. |
| Decrypt only files with extension .encrypted | Only files with the extension ".encrypted" will be decrypted. Decrypted files with the ".encrypted" extension will be renamed and have the ".encrypted" extension removed. Files without the ".encrypted" extension will be unaffected. |
| Decrypt all files | Decrypt all files in the selected folders. Decrypted files with the ".encrypted" extension will be renamed and have the ".encrypted" extension removed. Files with any other extension will be renamed and have the ".decrypted" extension added to their names. |
| Operation Controls |
 |
|
| and also |
 |
|
|
These controls are used to control the operation of the module and thus directly affect results. In order to restore the original data these parameters (and the password/key) must be the same as the ones used to encrypt the data.
|
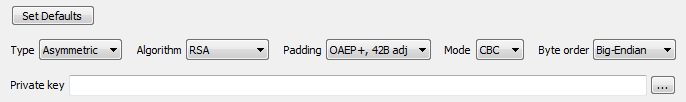
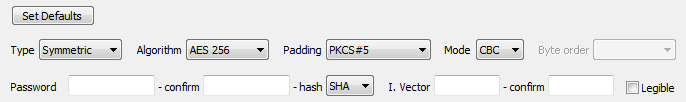
| Type | Select the type of decryption required. |
| Asymmetric | Use an asymmetric encryption algorithm to decrypt the data. |
| Symmetric | Use a symmetric encryption algorithm to decrypt the data. |
| Algorithm | Select the particular algorithm to encrypt the data. |
| RSA | - asymmetric - Public-Private Key pair algorithm (AKA RSA). Key size should be larger than 1024 bit (128 byte), key sizes are currently typically between 1024 and 4096 bits (128 to 512 bytes). |
| AES 256 | - symmetric - AES (Advanced Encryption Standard aka Rijndael) block encryption algorithm with 256 bit key size. |
| AES 192 | - symmetric - AES (Advanced Encryption Standard aka Rijndael) block encryption algorithm with 192 bit key size. |
| AES 128 | - symmetric - AES (Advanced Encryption Standard aka Rijndael) block encryption algorithm with 128 bit key size. |
| RC2 | - symmetric - RC2 block encryption algorithm. |
| RC4 | - symmetric - RC4 stream encryption algorithm. |
| DES | - symmetric - DES encryption algorithm. |
| 3 DES | - symmetric - The DES encryption algorithm internally applied three times. |
| 3 DES 2 Key | - symmetric - Two key triple DES encryption algorithm with a key length of 112 bits. |
| Padding | The encrypting algorithms require the data which is being encrypted to be of a particular size. To adjust the size of the data to that required, the system may have used padding while encrypting it. Select the padding mechanism that has been used to encrypt the data. |
| None; 11B adj | - asymmetric - Use basic padding. |
| OAEP+, 42B adj (aka: PKCS#1v2) | - asymmetric - Use Optimal Asymmetric Encryption Padding. |
| PKCS#5 | - symmetric - Use PKCS#5 padding. |
| Cipher Mode |
Encryption and decryption work on blocks of data. This option controls how these blocks will be mixed. |
| ECB | (electronic codebook) - the simplest mode - each block of data is encrypted independently. |
| CBC | (cipher-block chaining) - uses an initialization vector, stronger than ECB, similar to the CFB mode. For symmetric encryption, the user must know the secret initialization vector. For asymmetric encryption the user is not concerned with the initialization vector, however for software developers: the initialization vector is produced by repeated concatenation (to match the size of the modulus and when required removing the extra data at the end) of the big-endian SHA1-256 hash of the public key used to encrypt the data. |
| CFB | (cipher feedback) - uses an initialization vector, stronger than ECB, similar to the CBC mode. Not applicable for asymmetric encryption. |
| Byte Order | When blocks of data are encrypted, they can be stored in one of two directions. Different platforms work with one of these directions. Choose the same direction as the one used when encrypting the data. |
| Big-Endian | Blocks of encryption data were stored in Big-Endian byte order. |
| Little-Endian | Blocks of encryption data were stored in Little-Endian byte order. |
Private Key
(Used for asymmetric (RSA) encryption.) | Select or enter the path to the Private Key that is to be used for decrypting the selected items. This key must be the complement of the Public Key that was used to encrypt the data. Remember to keep Private Keys safe and secret until such time as they are to be destroyed using True Delete. |
Password
(Used for symmetric encryption.) | Enter the password that is to be used to decrypt the data. |
| Confirm [Password] | Enter the password again to confirm it. |
| Hash | The symmetric algorithms work with keys of particular sizes. In order to make any user-entered passwords usable, it is hashed, and the hash is further used to produce a key with size appropriate for the particular symmetric algorithm. Select the hash algorithm that was used when encrypting the data. The same hash algorithm must be used for both encryption and decryption or else the data will not be decrypted successfully. |
I. Vector (Initialization Vector)
(Used for symmetric encryption.) | Enter the initialization vector, if applicable, which was used when encrypting the data. Entering another IV will result in failed decryption process. Initialization Vector (IV) is a block of data which is used to start the encryption with feedback algorithms. Using IV greatly strengthens the encryption, and although it is not absolutely required it is highly recommended that IV is kept secret and treated as a second "password". |
| Confirm [I. Vector] | Enter the initialization vector again to confirm it. |
| Legible | Toggle this checkbox to make the password and initialization vector readable or not. |
| Set Defaults | The Set Defaults is a user friendly button to set the Operation Controls to a default selection of properties in order help users who might find the settings confusing. |
| Destination Controls |
 |
|
|
These controls are used to direct the output location there the module will store the decrypted files.
|
| Destination | Select the output type and location. Each decrypted file will have the ".encrypted" extension removed, if it had it. If not, the extension ".decrypted" will be appended to its name. |
| Common Place | All decrypted files are stored in the selected target folder. Caution is required as encrypted files with matching names may overwrite each other. |
| Original Location | All decrypted files are stored in the folder where the encrypted (source) file is located. |
| Reflecting Tree | The same directory structure as the directory structure of the selected files and folders is replicated, starting from the selected target folder. The decrypted files are deposited in the newly created folders respective to the folder containing the encrypted. |
| at folder | Select folder to be used for the "Common Place" and "Reflecting Tree" options. |
| Further Actions Controls |
 |
|
|
These controls are used to help to automate some common activities after the process is successfully completed.
|
| Delete Source Items | Set this checkbox to request the module to send the source items to the Recycle Bin after a successful decryption process. |
| Confirm Delete [Source Items] | Set this checkbox to confirm the request to delete the source items after a successful decryption process. |
| Window Controls |
 |
|
|
These controls have generic meanings.
|
| On Top | Sets and clears the Always On Top flag on the window. This checkbox adds or removes the window from the group of Top-most windows. |
| OK | Commits to work and decrypts the selected items. Note, an Enter Key (password) dialog will be displayed first. |
| Cancel | Closes the window without doing any work. The last selected properties are stored. |