 |
|
The Act on File modules are data processing units which perform particular type of data manipulation or conversion, or deliver a particular type of service.
A module may implement multiple functionalities, embodying or related to the particular type of work that the module performs, including converse functionalities.
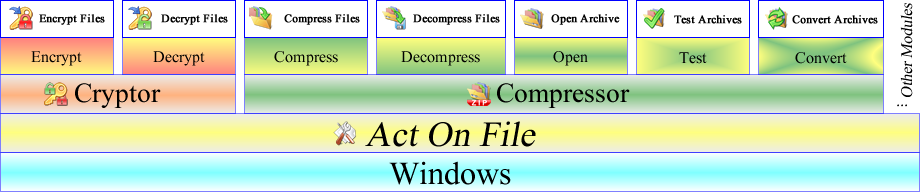
The different functionalities are accessed through dedicated windows which interface between the user and the underlying module. For example, the Cryptor module has
two interface windows to give access to two converse functionalities of the module, namely Encryption and Decryption. The Compressor module on the other hand implements
five functionalities accessed through their particular interface windows, which are Compress, Decompress, Open (Edit), Test and Convert. See the diagram below:
|
| Structure and workflow for the Cryptor and Compressor modules of Act On File |
 |
|
|
To perform a particular task on one or more files or folders, one needs to launch the appropriate functionality (i.e. window), supply the target files and folders, adjust any applicable
settings and start the task. Act On File 2012 has the following modules listed alphabetically:
|
 |
| The Attributor Module |
 - View and set file and folder attributes and file-times. Act on multiple items at the same time! - View and set file and folder attributes and file-times. Act on multiple items at the same time! |
|
|
|
The Attributor module is used to view and set generic attributes and file-times (filetimes) of multiple files and folders simultaneously. Generic attributes of files and folders are properties
such as the visibility (hidden or non-hidden) attribute, write permission, various file-times etc, and attributes which are dependent on the underlying file system such as files and folders
compression on the storage device, encryption on the storage device and others. Note that such compression and encryption is done by the file system internally and is not related to compression
and encryption performed by applications such as Act On File, WinZip, WinRAR and others. Some of the properties which are handled by the Attributor module are also adjustable through the File
Properties dialog in Windows Explorer.
|
|
Go to the Attributor module pages
|
|
|
The Authenticator module is used to confirm or deny the identity, authenticity and integrity of files, data and entities (people, companies, etc). When receiving any important information,
data or executable file, it should be authenticated and established that it is original (not produced by an imposter) and it has not been altered (intentionally or otherwise). An example
when authentication is necessary is when receiving important data via email. If the content of the email does not raise immediate doubts, most people authenticate the message and data
implicitly by comparing the email address of the sender with the email address that they expect to see. However, this is flawed since one can easily place whatever sender address they like
by manipulating their email server. Such attacks are called Phishing and Spoofing and can be directed to exploit the recipient, the supposed sender, entirely unrelated third parties, or all
of them. The Authenticator module of Act On File can be used to protect from such attacks, by digitally signing the data by the sender and authenticating it by the recipient. Another common
example for authentication is to digitally sign the testimonials placed on a website. This allows the visitors of the website to automatically verify the testimonials and be sure that they
are genuine and not made up. There are multiple other cases when it is important to establish the authenticity of data or document for which the Authenticator module can be used. Sometimes
the authentication process may deal with establishing the integrity of a file, rather than its origin. For example, that a file has not been corrupted by errors during storage or transmission.
A step-by-step technique on how to exchange information online safely is described in the Exact Steps to
Exchange Emails Safely protocol. The mechanism for authenticated website testimonials is explained step-by-step in the
How to Make Your Website Trusted protocol.
|
|
Go to the Authenticator module pages
|
 |
| The Comparator Module |
 - Compare files, folders and file properties. Find different or duplicated files fast! - Compare files, folders and file properties. Find different or duplicated files fast! |
|
|
|
The Comparator module is used to compare files, folders and file properties, and easily identify different or duplicated files and folders. The Act On File Comparator module
has a unique, easy-to-use design. The typical operation of the Comparator module involves selecting the items to be compared, choosing the property to compare, and starting
the comparison process. After the comparison is complete, the results are displayed in the results window together with the compared files and their properties. By selecting
rows in the result window, the user groups the files and properties ready to be acted upon. The results from the latter grouping are also displayed in the matches/aggregation
views from where the user can also act upon them.
|
|
Go to the Comparator module pages
|
 |
| The Compressor Module |
 - The ultimate Zip Archiver - do everything with archives. Work with multiple archives simultaneously! - The ultimate Zip Archiver - do everything with archives. Work with multiple archives simultaneously! |
|
|
|
The Compressor module of Act On File is an archiver software alternative to other archiving software such as WinZip and WinRAR, and is used to compress files and folders and create, edit, test, convert,
branch and perform many other operations on archives. Compressing a file makes said file smaller without losing information and requires decompressing the file before using it. Act On File uses the most
popular compression algorithms: zip, bzip2, store and [best] - utilizing the most appropriate algorithm for the particular data. Future versions will include additional algorithms. The Compressor module
has five functionalities, one of which - Compress Files, is used to create and update archives with full control over the process directly from Windows Explorer, and without the need to open the archive.
Decompress Archives allows the decompression of multiple archives with a single action. Open Archive is a full-scale archiving software, the equivalent of the popular archiving software applications,
allowing complete control over the opened archive and more. Open Archive also has a built in jukebox player allowing the user to play their music and videos directly from within an archive without the
need to first decompress them. The Test Archives functionality allows to test the integrity of multiple archives with a single action. The Convert Archives functionality is used to convert one or more
archives with a single action.
|
|
Go to the Compressor module pages
|
 |
| The Cryptor Module |
 - Encrypt and decrypt files. Generate keys. Protect your private information from theft or becoming public! - Encrypt and decrypt files. Generate keys. Protect your private information from theft or becoming public! |
|
|
The Cryptor module is used to encrypt and decrypt files and data. When information is encrypted it cannot be read until it is decrypted. Encryption must be used whenever one stores or moves
any kind of private data on a local machine, removable media (flash drive, CD, DVD, etc), or it is transmitted over the internet. For example, an email message is just like an open postcard
which everyone in the message path can read. The difference is that an email and the data attached to it can be also easily monitored and copied by numerous computers on the internet. Similarly,
when travelling and carrying private information on a removable media (e.g. a flash drive), it is important that the information is encrypted so that if the drive is lost or stolen then the data
is not intelligible to the person who finds it. Important private data should be kept encrypted even when held on a desktop system to protect it from the possible threats of burglary and some
types of spying software which may infect a computer. Encryption can sometimes be cumbersome as encrypted data needs to be decrypted before use, and then re-encrypted if it was modified. However
using Act On File to encrypt and decrypt data is simple and straightforward, yet it is very cryptographically powerful. Act On File supports the modern cryptographic algorithms. Using asymmetric
encryption gives strongest protection and allows exchange of encrypted data using private passwords, i.e. without requiring a common password. The maximum size of the key supported by Act On File
is 16384 bit (or 2048 byte), currently 2048 bit (512 byte) key is considered strong. In difference symmetric encryption uses a single password for both encryption and decryption. Act On File
supports the strongest known symmetric algorithm - AES, as well as number of other strong symmetric encryption algorithms.
A step-by-step technique on how to exchange information online safely is described in the Exact Steps to Exchange
Emails Safely protocol.
|
|
Go to the Cryptor module pages
|
 |
| The Eraser Module |
 - Truly destroy files, temporary and unknown files, file scraps, and the data of whole drives. A true data eraser! - Truly destroy files, temporary and unknown files, file scraps, and the data of whole drives. A true data eraser! |
|
|
|
The Eraser module is used to truly destroy information. When a file is deleted, it is moved to the Recycle Bin, which is almost an ordinary folder with this special name and an icon which
looks like a bin. When the Recycle Bin is emptied, the files seem to have been deleted. However, they are not destroyed, but merely marked as "deleted". The actual deletion occurs "by chance",
on a non predictable basis, when new data is added to the disk and may not happen long after the Recycle Bin was emptied or even never. There is specialized software which can be used to recover
deleted files, as well as companies that specialize in physically recovering information. The Eraser module of Act On File has four functionalities to destroy data. The True Delete functionality
truly and irrecoverably destroys files and folders, by overwriting their content with random data one or more times and changing all properties and names, which makes them unrecoverable and
unrecognizable. The Erase Scraps functionality truly destroys any file remains, from non-true deleted files, which otherwise could be restored, as well as unknown and temporary files. For example,
while working on a private document the word processor creates temporary copies of the document, which are generally unknown. However they can be destroyed using the Erase Scraps functionality.
The Erase Drive functionality truly destroys all information on entire drives. The Fast Delete functionality deletes files normally but without first depositing them in the Recycle Bin.
|
|
Go to the Eraser module pages
|
 |
| The Locator Module |
 - Ultra-powerful desktop search engine! Ultra-fast navigation to files and folders! - Ultra-powerful desktop search engine! Ultra-fast navigation to files and folders! |
|
|
|
The Locator module is used to easily locate files and folders. It consists of several diverse functionalities related to the location of files and folders. The Find Files and Folders functionality is
the most powerful desktop search engine, used to find files and folders located on the local computer or network. The user first easily creates one or more Find Operands which they then use in their
search queries. Find Operands are stored and can be used in multiple searches until deleted. When created, Find Operands are assigned type, name and data (if applicable). The type of the Find Operand
determines what property of a file or folder it represents, and will be used to match in the scanned files and folders. The type of the Find Operands could be virtually any property of a file e.g.
filename, extension, content, size, meta-property – i.e. author of a document or height of an image, and so forth. Depending on the type of the Find Operand, it might require some data. For example,
if the Find Operand represents the height of an image, then the user must set the height they are looking for. The user then uses the names of their Find Operands to create a search query using logical
operators AND, OR, XOR, NOT and brackets. For example, if ImageHeight1 is the name of a Find Operand of type "image-height" and has data 480, and ImageHeight2 is another Find Operand of type "image-height"
and has data 640, then a search query such as [>ImageHeight1] & [<ImageHeight2] can be used to find all images with height between 480 and 640 pixels. Thus the Find Files and Folders functionality
can be used to easily find files with searches from the simplest to the most complex. The Navigate to Target functionality is used to locate previously appointed files and folders in a very fast fashion
without having to browse in Windows Explorer. Most computer users have some files and folders to which they regularly navigate, and often they create shortcuts on their desktop trying to minimize the
browsing through Windows Explorer. Using the Navigate to Target functionality allows quick navigation to these special locations with just 2 clicks from anywhere in Windows Explorer or from the
Act On File Icon on the system tray.
|
|
Go to the Locator module pages
|
|
|
|
The Protector module is used to protect the user’s files and folders from being lost due to hardware, software or human error. The Backup and Restore functionality of the Protector module is
used to create backups of files and folders automatically when they change, or at a specific time period - daily, weekly or monthly, or manually by explicit user request. The Backup and Restore
functionality works quietly in the background using negligible system resources, relieving the user from the task to manually maintain backups of their important data. The Backup and Restore
functionality compresses the data in an appointed backup container (an archive), and if requested, uploads the backup container to a private FTP location on the internet appointed by the user.
A single file or folder can be subject of multiple backup tasks, storing it in different backup containers for each task. A backup container can be the target container for multiple backup tasks,
and can be located on the local machine, local network drive or on an FTP server.
|
|
Go to the Protector module pages
|
 |
| The Quantifier Module |
 - Join and split files. Extract Data From Files. No more files being too small, too many or too large! - Join and split files. Extract Data From Files. No more files being too small, too many or too large! |
|
|
|
The Quantifier module is used to join, split and extract data from files. There are cases when, for various reasons, files have to be joined together (possibly in a specific order) or split into
smaller files. The Quantifier module offers two functionalities which make these two processes easy to do, while at the same time giving complete flexibility and power to the user. The Join Files
functionality is used to join two or more files and folders into a single file using variety of features and modes. The Split File functionality is used to split a file into many files using a
complete range of features and modes, or extracts data from a file.
|
|
Go to the Quantifier module pages
|
 |
| The Act On File TV Module |
 - Watch the news, seminars, tutorials and entertainment. Act On File TV brings information the way you want it! - Watch the news, seminars, tutorials and entertainment. Act On File TV brings information the way you want it! |
|
|
|
The Act On File TV module is free software which brings news, seminars, tutorials and entertainment classified for easy access.
|
|
Go to the Act On File TV module pages
|
|